5 Tips for Keeping your Data Secure
Step 1: Ensure that your data is kept under lock and key
Strong Passwords Make Strong Defences
The key to keeping your data safe is making sure that it does not fall into the wrong hands. A strong password is the first step when it comes to stopping people from stealing your confidential information. If your password is not strong enough, hackers can easily get into your system to steal your personal data. Make sure that your passwords are changed regularly to keep your systems safe.
How do hackers get into your system?
There are several methods that hackers will use to try and access your system. Understanding these methods will help you to protect against them. This will give you an insight into what the main threats are to your cyber security.
- Brute Force Attacking – Hackers will try to crack your password by guessing. They will therefore try generic passwords first to try and gain access to your system. Examples of generic passwords include ‘Password1’ or passwords that contain personal information, such as your name or your company. Most of these attacks use automated processes to attempt different combinations of words and numbers. Ensure that your passwords are difficult to guess to keep your data safe.
- Dictionary Attack – This is very similar to a brute force attack as hackers will try to guess your password. However, instead of trying common passwords, they try a much larger selection of words. Effectively, hackers will run a system which tries random combinations of common words or phrases. Therefore, passwords with common phrases are high risk. Make sure that your passwords are unique so that they are much harder to crack.
- Phishing Scams – The most common type of cyber-attack, phishing scams usually take the form of emails sent to employees. This usually involves an unverified link or document. These links typically contain malware which will infect your system. Clicking on a link or document gives hackers a backdoor entrance to your internal systems and data.
What Makes a Password Strong?
In order to keep your data safe from hackers, it is essential that your employees use strong passwords. Since hackers will often try a series of common words and phrases, passwords should not be overly simple. This means making sure that passwords contain a mixture of upper- and lower-case letters, numbers, and symbols. This will protect you against the two most common types of attacks: brute force and dictionary attacks. Encourage your employees to set longer passwords as these are much harder to crack. Have an internal password policy to ensure that everyone is setting strong passwords.
Take Extra Precautions
Adding an extra step to your security process can save your data. Where possible, use two-factor authentication. Most services offer this as standard, including Google and Microsoft. It works by sending a text to your personal mobile when a new device signs into your account. Two-factor authentication means that even if hackers manage to crack your password, they will not be able to access your private information. Use password managers to avoid data leaks. Password managers allow you to use much stronger passwords without having to remember them. Once you log in to a password manager, you will have access to all of your passwords for your websites and subscriptions. Most password managers will provide suggestions for strong passwords when you sign up to a new website. Google has now built this into their service which helps improve your cyber security.
Step 2: Train Your Staff to Understand Cyber Threats
Train Your Staff to Stop Data Leakage
Your employees are most at risk of giving away sensitive information about your company. Proper training is key to stopping your employees from leaking your data. Ensuring that everyone at your company understands the threats to your cyber security is therefore vital. Make sure to train your employees throughout the year. In particular, make sure your employees are aware of any new cyber threats as they are uncovered. This could include new phishing scams which are one of the biggest threats to the security of your data.
What is a phishing email?
All companies will have to face phishing emails on an almost daily basis. Here are some of the warning signs to look out for:
- Abnormal email addresses – Avoid clicking on any links from unfamiliar email domains. If you do not recognize the sender, do not open the link. An unfamiliar email domain is the biggest red flag that you have received a phishing email.
- Spelling and Grammar Mistakes – Be aware of emails that contain typos or poor grammar. If an email seems to come from a reputable company but is littered with these errors, it is likely a phishing email. Additionally, be conscious of the formatting used in the email. If you receive an email that differs from emails you have previously received from a company, report it to your IT manager. Hackers will likely slip up in this area and follow a different style to the company they are impersonating.
- Strange Openers – Most of the time emails will open with a personalized greeting when sent to your private email. For example, most emails will begin “Good Morning Mr Smith” or “Hello John”. Typically, phishing emails will be sent to a large database of people. This means that emails will not be personalized to you. Therefore, if an email begins with a more generic greeting, be wary. Avoid clicking on links in emails that begin “Dear Sir/Madam” unless you recognize and trust the email address.
- Double Check Link URLs – Before you click on a link, check that it comes from a trusted domain. For example, if you receive a link to a company website, make sure that the URL matches the company name. If you are ever in any doubt, do not click on the link.
Anatomy of a Phishing Email
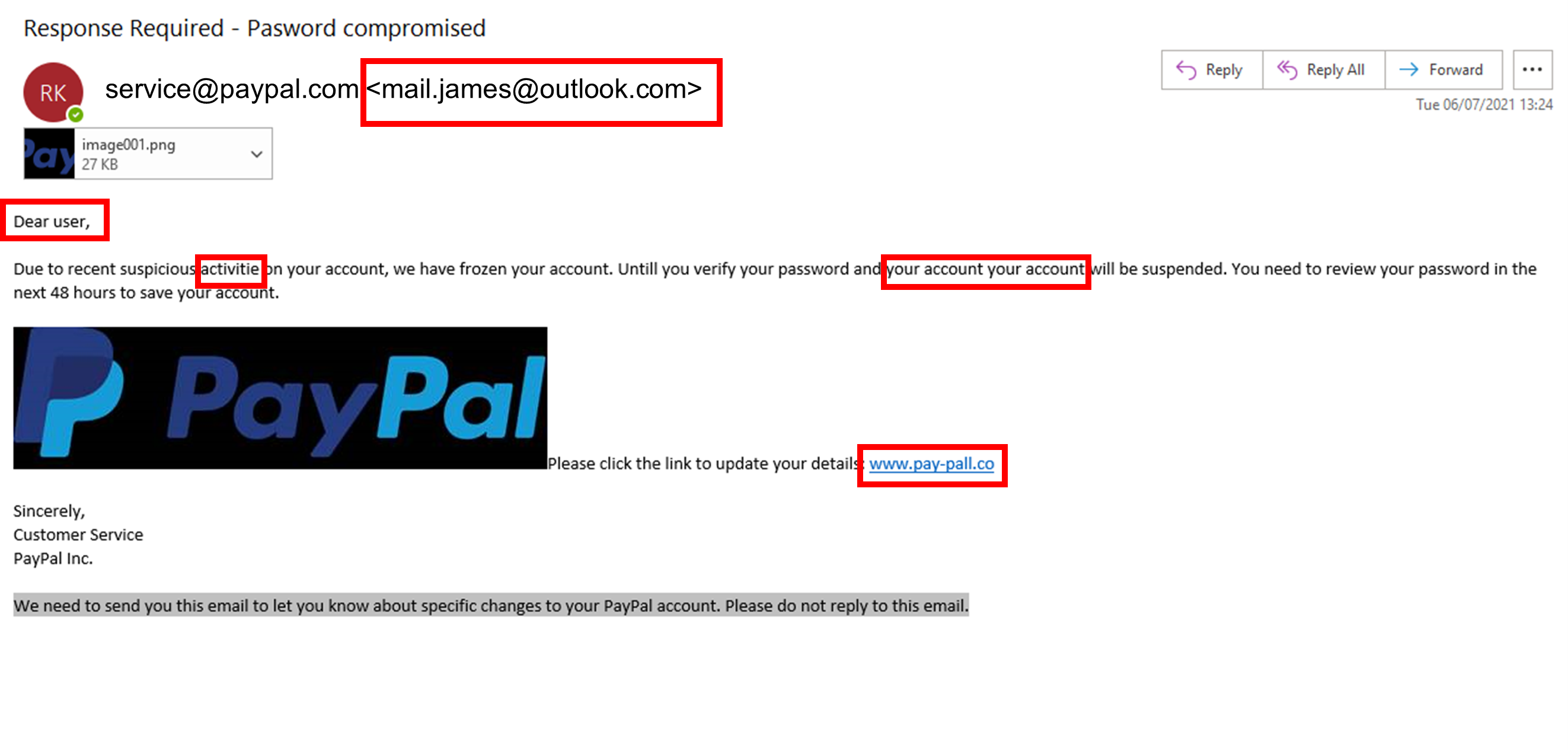
Tip 3: Track and Trace your Data
Keep Information on a Need to Know Basis
As stated before, your people are one of the biggest risks to your cyber security. Therefore, you should restrict access to certain documents and folders on your servers. By restricting access to these files, you ensure that your data does not fall into the wrong hands. This means that your employees cannot gain access to confidential information that does not relate to their job role. This is important as it limits the volume of information available to hackers in the event of a cyber-attack.
Track your Files and Servers
In addition to limiting access to certain files, ensure that you are tracking who accesses each document. This can provide you with insight into any potential data breaches. Using file auditing software allows you to monitor any unusual behavior in your internal systems. In the unfortunate event that you are victim of a cyber-attack, tracking your files can help you figure out which accounts have been breached. This will also help you to determine what information has been compromised.
Back Up your Data Regularly
Ensure that your data is backed up regularly. In the event of a cyber-attack, you will still have vital information that you need to continue with business as usual. Cloud-based solutions are the most efficient solution for this. These allow you to back up your data regularly and efficiently. Backing up your data also helps in the event of a systems failure.
Tip 4: Data Protection While Working from Home
With working from home (WFH) becoming the standard for a lot of organisations, it is important to understand the potential risks that come with this new style of working. Ensuring that you protect the privacy of your employees while they work at home is essential.
Firstly, you should ensure that your employees connect to your servers using a Virtual Private Network (VPN). This makes sure that their connection to the internet is secure. VPNs provide a more secure, encrypted connection for your employees, keeping your data safe. Also, make sure that confidential information is not being shared with other members of the household. Remember, information should be on a need-to-know basis.
Tip 5: Securely Dispose of your End-Of-Life IT
Protection from Cradle to Grave
The previous tips have looked at protecting data on your active IT equipment. However, it is equally important to ensure that your data is erased when you dispose of your IT equipment. Therefore, you must securely erase any traces of your data from your IT equipment at the end of its use. IT Asset Disposal companies, or ITADs, provide these services or you. ITADs will securely erase your data in one of two ways.
Firstly, using government-certified data erasure software known as Blancco, ITADs can securely wipe your data from a hard drive. This software erases every sector of your hard drive to ensure that all of your confidential information is removed.
Secondly, ITADs can shred your Hard Drives. Using government-approved hard drive shredders, ITADs are able to shred your data-bearing assets down to as little as a 6mm shred size. This makes it impossible for anyone to recover data from your old hard drive.
Why is Secure Data Erasure Important?
Although you may be finished with a laptop or PC, others may be interested in gathering the private information stored on them. Therefore, it is essential that all data is erased from a device. If residual data remains on a device, hackers could begin to piece this together. For example, one saved password on a laptop could compromise your entire future IT estate. Therefore, it is vital to your cyber security that you take care of your end-of-life IT assets.
Which ITAD should I use for Data Erasure?
When selecting which ITAD to use, there are several key aspects to consider:
- Accreditation – In order to ensure that your data is in safe hands, you should work with an ITAD which has the proper accreditation. Accreditations provide you with the peace of mind that an ITAD has been audited. This ensures that they are following the proper practices.
- Experience – By working with an ITAD with a long history in the industry, you ensure that your data is being cared for by experts. Firms with more experience in the industry will have more streamlined processes and better security for your data-bearing assets.
- Reporting – You should only trust ITADs which will provide you with a suite of reporting throughout the data erasure process. This provides you with evidence that your data has been erased fully. Without data sanitisation reports, you would not be able to prove that your data has been handled safely.
Re-Tek are one of the most accredited ITADs in the UK and are able to provide a solution to your IT asset disposal needs, no matter how big or small. With 25 years of expertise in the industry, Re-Tek will ensure that your data is handled securely and will provide you with a suite of reporting proving that all services have been carried out properly. To view the range of services Re-Tek offer, click here.